Setting up rate limiting via WAF
If your infrastructure setup is such that all of your site visitors are coming to your website through a CloudFront distribution as the first point of contact, then you can use WAF to reliably rate limit requests from visitors.
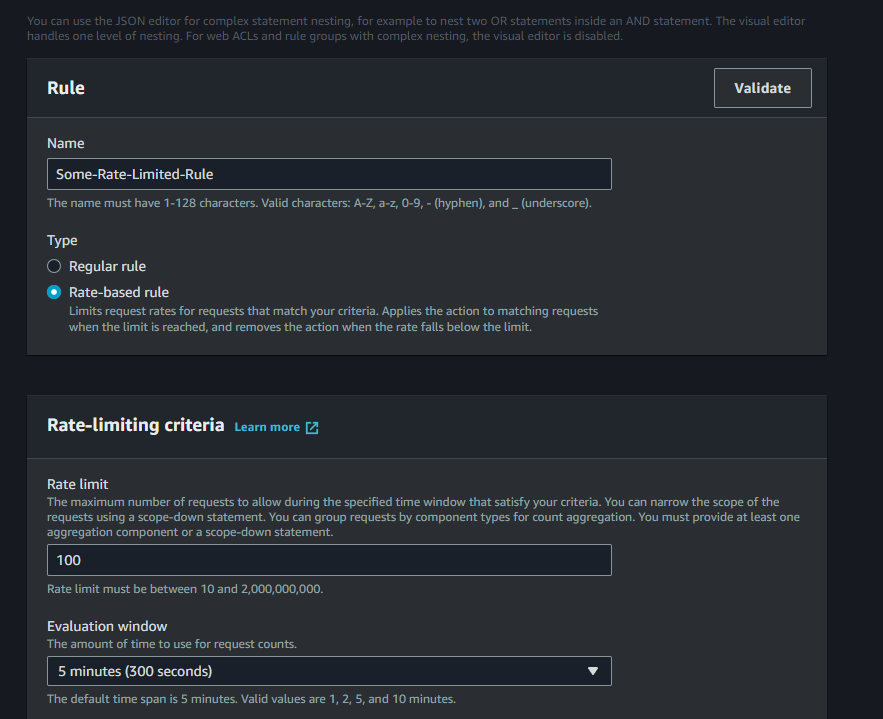
Adding a rate limit rule
To add a rate limited rule, go to "Rule Groups" in the WAF Console and click "Add Rule" in an existing rule group (you can create a new rule group now if you need to).
Choose "Rate-based rule" as the rule type, and then select a rate limit and an evaluation window; it's a rolling window, so this lets you set how often visitors can request pages.
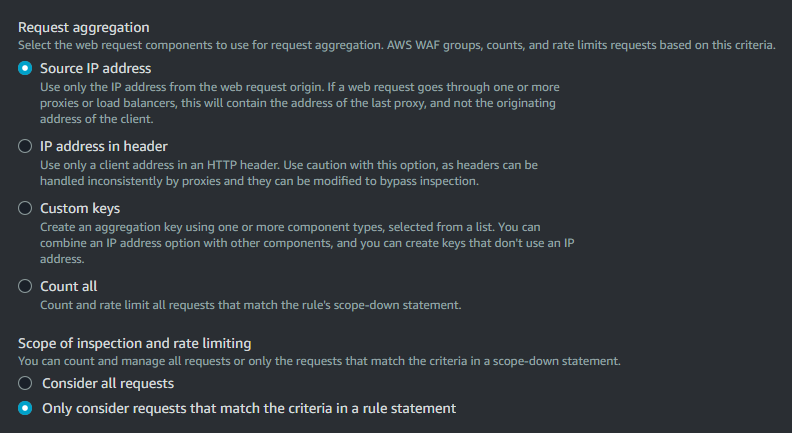
Under "Request aggregation", choose "Source IP address". Since there is no proxy or load balancer the visitor uses before CloudFront (other than e.g. their own proxy), this is reliably going to be their IP address for all practical purposes.
For "Scope of inspection and rate limiting", select "Only consider requests that match the criteria in a rule statement".
If you use "Consider All Requests", all AJAX forms that are submitted on page load will be counted in your rate limit, likely causing your users to get heavily throttled out of viewing your website!
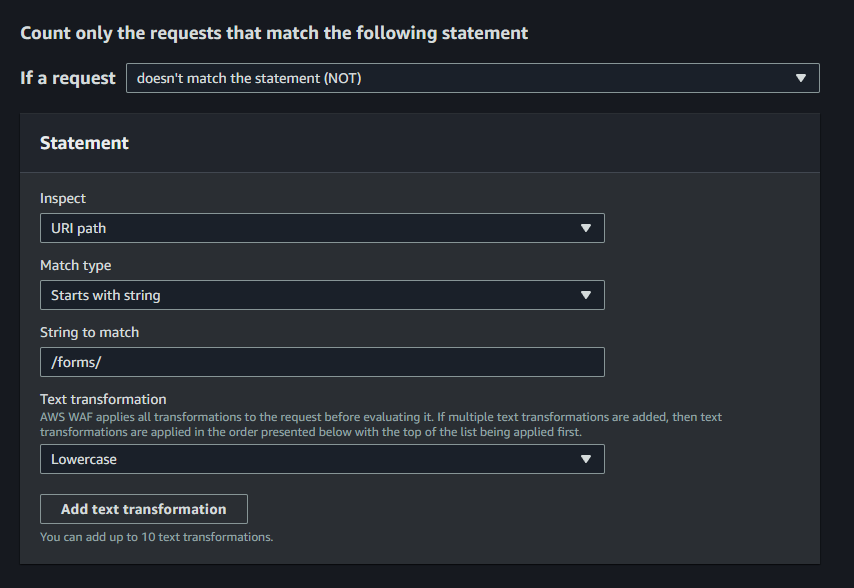
Now, we need to specify the criteria for considering requests as counting towards the rate limit. In the below example, we have set the criteria such that any page request that does not start with "/forms/" will be counted; for Deserted Chateau, the "/forms/" directory is where all AJAX forms are located, so we want to exclude them from being counted towards rate limiting.
Since some pages, like galleries with infinite scroll, can potentially have a huge number of AJAX requests on a single page if the user scrolls for ages, we can choose to make a separate rule to handle rate limits for the "/forms/" URI prefix, but we don't want to it to be part of this rule.
Note the Lowercase text transformation. We don't want requests that somehow ended up being written with "/Forms" or similar to be counted towards the rate limit; if we don't have this text transformation, then they'll be counted when they shouldn't be.
If you get the error below, it means your WAF Rule Group doesn't have enough capacity to add the rule. You'll need to make a new rule group with sufficient capacity, then add your rule to it, and then add that rule group to your web ACL.